University of Texas team takes control of a yacht by spoofing its GPS
By Brian Dodson
August 11, 2013

The 213-foot White Rose is the US$80M megayacht whose GPS navigational system was spoofed by about $2,000-$3,000 worth of equipment (Photo: U of Texas at Austin)
Civilization depends on the Global Positioning System for everything from precision armaments to finding the location of the nearest pizza shop. Indeed, access to GPS's strengths and capabilities has grown so fast that little concern about its weaknesses has penetrated the public consciousness. Fortunately, assistant professor Todd Humphreys' team at the University of Texas at Austin continues to arrange splashy demonstrations of GPS spoofing. His latest is to covertly alter the course of an oceangoing yacht.
The Global Positioning System (GPS) is made up of a constellation of satellites and ground stations, the satellites continually transmitting the current time and their location in orbit. Even though the transmitted power is only about 10-16 watts, the extraordinarily sensitive GPS receivers in many cases can detect multiple GPS signals from an indoors location.
Given such signals from four GPS satellites, the time interval between sending and receiving the signals reveals how far away the satellite is from the GPS receiver. Added to information pinpointing the orbital locations of the GPS satellites at the time of transmission, this is enough information to locate the receiver to within about a 5-meter (16-foot) circle on the Earth's surface. The delicacy of the location task is illustrated by the fact that, were corrections for general relativity ignored, the resulting position error would increase by about 10 km (6 miles) per day.
This summer, Professor Humphrey's group was invited on board the White Rose, a US$80M, 213-foot (65-meter) superyacht, to attempt to capture control of the large ship via GPS spoofing. Having previously captured a GPS-guided unmanned aerial vehicle (UAV), Humphreys and his group are continuing their mission to show that GPS spoofing is dangerous to all GPS-directed modes of transportation.
A GPS spoofing attack works by diverting the attention of a GPS receiver so it locks onto a fraudulent GPS signal that appears to have been received from the GPS satellites. This is accomplished by constructing the fraudulent signal, and slowly increasing the power of its transmission. When the spoofing signal is stronger than the real signal for one or more of the GPS satellites, the receiver only detects and reads the stronger signal.
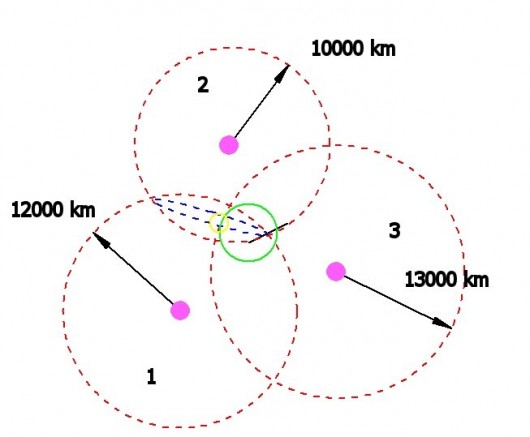
As illustrated above, a GPS receiver determines its location by measuring the distance from three satellites in orbit around the Earth (four are needed for determination of a unique location, but drawing this would obscure the figure). The receiver is located 12,000 km (7,456 miles) from satellite 1, 10,000 km (6,214 miles) from satellite 2, and 13,000 km (8,078 miles) from satellite 3. The blue ring is the locus of points which are the correct distances from satellites 1 and 2. The green circle is the Earth's surface, and the intersection of the locus of points 13,000 km from satellite 3 and the blue ring identifies a maximum of two points, one of which must be the location of the GPS receiver. Including distance from a fourth satellite removes this dichotomy, and also makes the calculated location more robust against noise.
A spoofing signal contains information consistent with the real signal from one of the GPS satellites, but alters the apparent distance between that satellite and the receiver. As a result, the 3D quadrangulation process used to determine the location of the receiver will give the wrong answer and that answer will be wrong in a predictable manner. In other words, the apparent location and course of a GPS-guided vehicle can be changed nearly at will with rather simple equipment.
A GPS spoofing attack begins by broadcasting a slightly more powerful signal that initially agrees with the correct position of the GPS receiver, and then slowly alters the apparent position of the vehicle. The spoofer's adjustments must be sufficiently slow that the receiver does not lose signal lock – it must lock onto the spoofing signal without noticing the signal is different.
“With 90 percent of the world’s freight moving across the seas and a great deal of the world’s human transportation going across the skies, we have to gain a better understanding of the broader implications of GPS spoofing,” Humphreys said. “I didn't know, until we performed this experiment, just how possible it is to spoof a marine vessel and how difficult it is to detect this attack.”
At a point some 30 miles (48 km) off the coast of Italy, graduate students Jahshan Bhatti and Ken Pesyna began to send a faint set of GPS spoofing signals from their briefcase-sized transmitting device on the upper deck of the yacht. As they increased the strength of their signals, the ship's GPS location system eventually was thoroughly spoofed – paying attention only to the UTexas team's spoofing signals.
At this point, the indicated course of the yacht was altered by a few degrees, although the ship had not actually turned. The spoofed GPS then reported a difference between the ship's location and the desired course, and altered course to return to the correct course. Of course, in doing so it took on a course that same few degrees different from the proper course. By continuing to maintain this discrepancy, the yacht showed in its wake that the ship was turning, even though the electronic chart of the navigational system showed the ship was on a steady course. This is shown in the form of an animation in the video below.
“The ship actually turned and we could all feel it, but the chart display and the crew saw only a straight line,” Humphreys says. “This experiment is applicable to other semi-autonomous vehicles, such as aircraft, which are now operated, in part, by autopilot systems. We’ve got to put on our thinking caps and see what we can do to solve this threat quickly.”
Source: University of Texas at Austin